

E-commerce security might not be the first thing that comes to mind when thinking of customer experience, but for B2B organizations, a secure web store is vital to maintaining strong customer relationships. A loss of data can result in a negative impact on trust and lead to irreparable damage.
Here’s everything you need to know about the security measures that will keep your business resilient to attacks.
What is e-commerce security?
Broadly speaking, e-commerce security refers to a set of globally accepted guidelines that ensure safe purchasing experiences on the internet. These include protocols that protect both the businesses selling their products online, as well as the customers sharing their personal information to purchase these goods.
There are a few different facets of e-commerce security that are important to familiarize yourself with as you establish the types of protocols that are necessary within your own web shop. These include:
- Authentication, which establishes that both buyer and seller are verifiable identities, who are who they claim to be.
- Privacy, which refers to the protection of customer data, especially from unauthorized third parties.
- Integrity, which means this data will remain unedited or altered in any form, and
- Non-repudiation, which is the legal principal that enforces follow-through on a transaction.
E-commerce security glossary: Terms you should know
When trying to establish security measures for your own web store, it’s easy to get thrown off by acronyms or technical jargon. Here’s a quick overview of some of the most common terms to familiarize yourself with:
- International Organization for Standardization (ISO): The ISO is an international body that guides businesses in making sure their products and processes are up to standard. The ISO/IEC 27001:2013 in particular covers data security, and a certification for this means your business has verified and high-standard risk-aversion strategies.
- Payment Card Industry Data Security (PCI DSS): Commonly known as PCI, this industry standard relates to the protection of credit card information.
- Multi-factor authentication / 2-factor authentication / 2-step verification (MFA, 2FA, 2SV): These forms of authentication go beyond simple log-in for verification. With 2SV, users enter a one-time code delivered via an email, text message, or call. 2FA involves the user to login to a secondary device, using an app or logging in from a laptop.
- Transport Layer Security / Secure Sockets Layer / Hypertext Transfer Protocol Secure (TLS, SSL, HTTPS): These security certificates ensure e-commerce security to customers visiting your website and serves as additional verification that your site is safe.
10 common e-commerce security weaknesses & attacks
The statistics on cyber-attacks are troubling – in 2021, 50% of all cyber-attacks were done on SMBs. Why is that? Because e-commerce sites are rich sources of data, sensitive information and capital. For nefarious actors, exploiting e-commerce security weaknesses is a lucrative business.
These weaknesses can take many forms – insider threats, customer threats and even natural disasters. Protecting against these e-commerce security threats requires a broad set of tools that must be updated and maintained rigorously to protect your company and your clients.
Let’s take a look at the biggest threats to your e-commerce security and how you can prevent them.
1. Phishing
Quick! What do you do when you get this email?
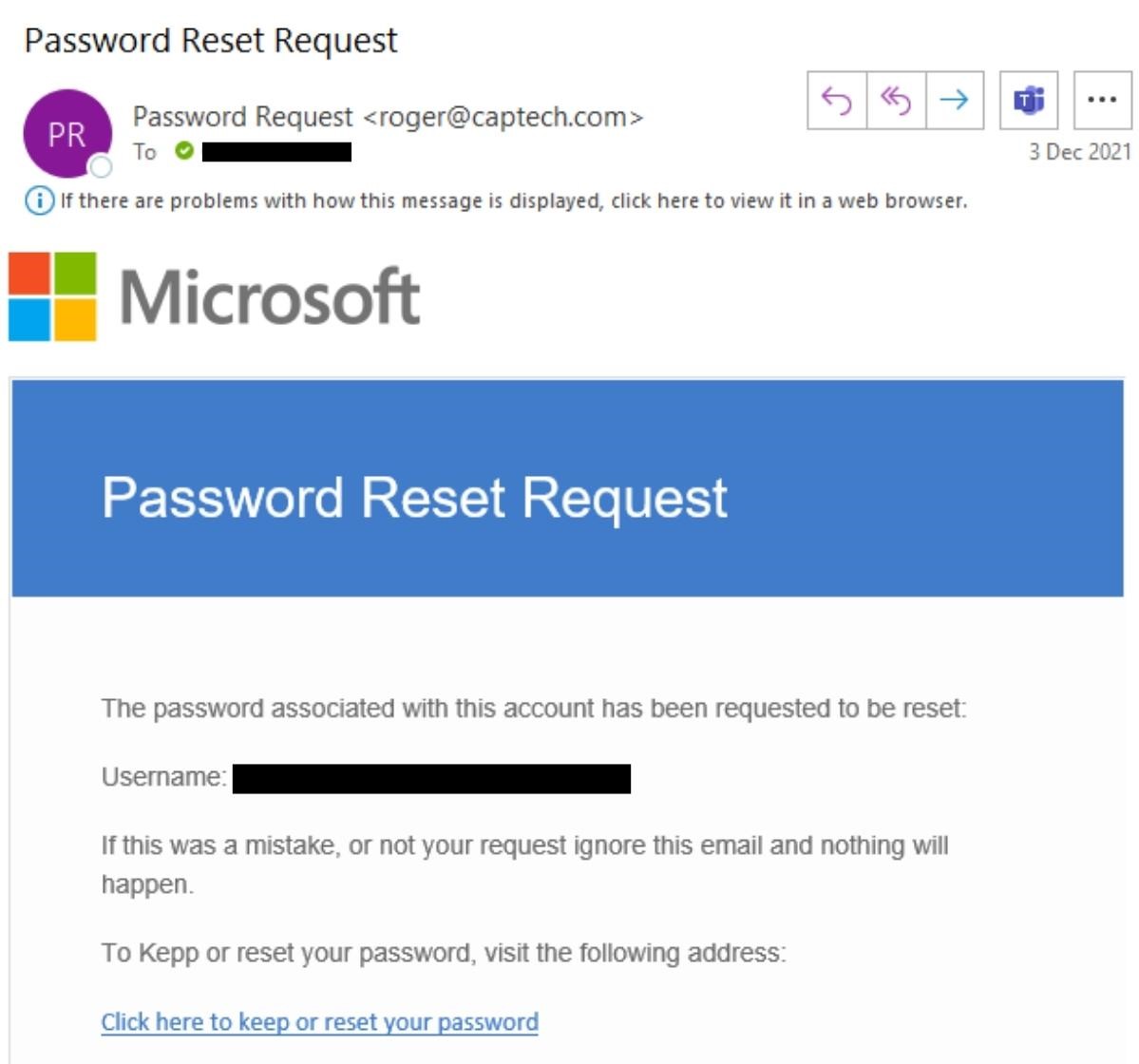
You might not think twice about clicking the link, since you have requested a password reset and are expecting an email about it.
But, since you’re smart, you take a moment, and go to the email address of the sender.
“roger@captech.com”
Wait a second. That’s not an email from Microsoft. That’s a fake email!
This is an example of a phishing scam. Phishing is where individuals are targeted with fraudulent, yet believable emails. The emails often pretend to be from authority figures (like CEOs) and often contain directions with urgency, such as “please take a look at this file right away.”
The victim will unwittingly click on the file, which ends up installing a nefarious program onto their computer. This program can steal documents and finances, causing significant damage.
Phishing is often caught by a good spam filter, but some messages can still get through. As spam filters become more effective, scammers have turned to text messages, sending “smishing” texts that goad you into clicking a dangerous link via text.
2. Malware & ransomware
Malicious software, commonly known as malware, is installed by attackers on your system. Ransomware is type of malware and involves locking a victim out of their own system, preventing access to data unless some kind of ‘ransom’ is paid out. Ransomware attacks have targeted banks, schools, and even hospitals – costing the world $21 billion in 2021. Here are some common signs you might be experiencing a malware attack:
- Being taken to the wrong links/page destinations
- Incessant pop-up ads that are difficult to click out of
- A slow system that is constantly crashing/freezing
- A high quantity of emails you send bounce back
- New icons showing up on your desktop without having been installed
3. Zero-day exploit
Zero-day sounds like something out of a spy thriller, but the reality is almost just as outrageous. A zero-day vulnerability is an unknown security flaw that someone can take advantage of. A zero-day attack or zero-day exploit is an attack carried out that exploits this unknown security flaw. Because the victim was unaware of the flaw before the attack, they aren’t able to release a patch to prevent the attack until it’s too late.
Zero-day exploits are particularly dangerous e-commerce security threats precisely because they rely on undiscovered vulnerabilities.
4. E-skimming
E-skimming is the digital version of credit card skimming. While in the physical world, skimmers are installed over credit card readers to skim credit card information, e-skimmers are pieces of malicious code that steals a customer’s credit card data during an online transaction. Using secure payment processors such as Sana Pay is a great way to reduce this e-commerce security threat.
5. Man in the middle attack
An MTM attack is what’s called an “active eavesdropping attack.” A third party intercepts a conversation or transfer of data between two parties. This third party can additionally inject malicious software into the files that are being exchanged, ultimately infecting further systems after the attack has been completed.
6. SQL injection attack
Most e-commerce sites maintain databases filled with customer information such as email addresses, physical addresses, phone numbers, etc.
A SQL injection attack allows an unauthorized user to access these databases. By using a nefarious piece of code, a hacker can bypass an authentication page, and gain access to the full back-end database. From there, the user can steal, modify and delete the data.
7. Cross-site scripting XXS
XSS or cross-site scripting is an e-commerce security threat where a hacker adds malicious code to a legitimate website. This code will then attack a user when that person browses the infected website.
XSS can result in client impersonation, keystroke logging, file/webcam/microphone access, and identity theft.
8. Financial fraud
Financial fraud is a different type of e-commerce security threat than, say, SQL injection. Instead of relying on malicious code, financial fraud relies on stolen credit cards or fake returns in order to benefit at the company’s expense. When credit card fraud is discovered, the e-commerce site will have to refund the victim without recouping the goods sold – leaving them on the hook for an expensive bill.
9. Insider threats
Insider threats are a serious danger for e-commerce businesses. Disgruntled employees (or ex-employees) may attempt to steal company data or proprietary information in hopes of selling it to a rival business. Or, they may attempt to lock or delete company data to cause your business to suffer. Either way, these insiders represent a real security threat in the e-commerce space.
10. User error
Sometimes, somebody messes up.
We’ve all been there. We click a button we weren’t supposed to. We change an element that wasn’t meant to be changed. Next thing you know, the entire website goes dark.
Whoops.
User error happens. People mess up. What’s important is to ensure that you have ample backups that let you get your site back online as quickly as possible.
The importance of e-commerce security
E-commerce security is always important — no one wants their order history or (shudder) their payment details leaked. Plus, you want your web store to be available when your customers need it. This is particularly important for B2B e-commerce.
Luckily, selling online doesn’t have to be a risky endeavor.
There are plenty of ways to strengthen the security of your e-commerce platform. Here are three technologies that can help you deliver a safe online shopping experience that your clients expect from their trusted business partner.

Make your e-commerce project a guaranteed success
Watch our on-demand webinar on the five pillars you need to ensure you’re on the pathway e-commerce success!
E-commerce security measures to protect your web store
E-commerce security threats are a constant menace. You need to actively defend against these threats to ensure that your users can safely browse your e-commerce site without fear of fraud or theft.
Here are some prudent steps you can take to reduce the risk of e-commerce security threat.
#1. Use closed source code
One of the first things to consider when purchasing new software is whether you want a solution based on open source or closed source code. But when it comes to open source vs. closed source, how can you determine which one is best for your B2B web store?
Open source code
Open source code is created by an open community of developers. There are no restrictions on who can contribute to the code’s ongoing development.
Software created with open source code is subject to constant peer review, and is therefore constantly developed by a “team” of thousands of developers, if not more. Sounds like the recipe for a bullet-proof B2B web store, right?
Not exactly.
That’s because it’s not actually a development team working on the software — it’s whoever wants to get involved. There’s no selection process, so anyone can contribute or even just view the code. That includes developers with less-than-noble motives.
Closed source code
When it comes to development, bigger teams aren’t necessarily better. Closed source solutions are only worked on by a select group of developers — “select” being the keyword.
Contrary to open source code, closed source code is proprietary and not open to the public, either to view or collaborate on.
While there are fewer sets of eyes on closed source code, those eyes belong to carefully recruited developers. Limiting the number of engineers and other specialists working on the software makes it easier to:
- Control the development environment
- Keep track of who has worked on what and with a smaller scope
- Prevent issues from slipping through the cracks
- Assess quality of the developers and of the product
#2. Ensure strong password creation
A simple tip that is often overlooked, ensuring both you and your customers have strong passwords can go a long way in securing your online portal. A strong password includes at least eight characters, that contain a mix of upper and lowercase numbers, letters and special characters.
#3. Install device protection
Installing a trusted anti-virus software, keeping networks secure with firewalls, and ensuring there are routine updates for these platforms will help add a secondary layer of security to your data, and prevent interference on your e-commerce platform.
#4. Set up a VPN (virtual private network)
A virtual private network, or VPN, provides a way to securely send data over the public, possibly unsecured networks like the internet.
Make no mistake, the internet is not always as safe as you think. Remember the Heartbleed Bug from 2014? Taking extra precautions against online hackers is particularly pertinent if your mission is to create a truly excellent online buying experience for your users and customers. Why? Because doing this takes a lot of information — information that you can’t afford to put at risk.
Setting up a virtual private network (VPN) connection helps you keep your connection secure and your data confidential.
You may be familiar with VPNs as a way to protect your privacy when using the internet. However, you can also use a VPN connection to protect your corporate network. In fact, VPNs were originally developed to let remote workers connect to their company’s network without compromising security.
If you use an ERP (enterprise resource planning) system with your online portal, VPNs can be used in the same way to safeguard your integrated ERP. Any data sent via a virtual private network is encrypted. For more information about how a VPN works exactly, we recommend this article by Microsoft.
#5. Use multi-factor authentication for added data protection
Multi-factor authentication (MFA) can be a valuable tool for e-commerce security, especially when it comes to protecting customer purchases and preventing loss of data.
#6. Create consistent backups
Site breaches can result in a loss of data – ensuring you regularly create backups will help minimize lead time to total recovery.
#7. Switch to HTTPS
HTTP is the standard way data is transferred on the internet. HTTPS provides a layer of encryption to this data. With HTTPS, you can prevent most man-in-the-middle attacks.
Every e-commerce website should use HTTPS at a minimum; many browsers will block a user from opening a non-HTTPS webpage.
#8. Implement a failover system
In 2013, Google went down for 5 minutes and global internet traffic plummeted by a staggering 40%. Can you imagine having to go longer than a few minutes without access to your key systems? No internet search, maybe no email, possibly even no access to your documents — and no YouTube to distract you while you wait for systems to be restored.
Your web store might not be quite as essential for your organization or your clients as Google’s entire service portfolio. After all, if the worst comes to the worst, your sales team can look up product data in the ERP, and your clients can still get in touch via the phone.
But think of how your clients would feel if they couldn’t get in touch with you through your regular channels. Like we mentioned above, you have worked hard to build up strong relationships with your client base. You don’t want to let spotty service erode this trust. And what if your clients are placing orders outside office hours, so they’re not able to simply call your sales reps?
An unavailable web store isn’t something you (and your clients) want to experience first hand.
Taking measures against unforeseen outages — especially during the peak-volume seasons — is just as vital as warding off data breaches, and a reliable way to do this is through failover systems.
A failover system lets you improve the availability of your e-commerce site by switching to redundant web store installations when your primary web store environment is unavailable. In this situation, redundancy is something to be celebrated: it refers to backups of systems or data that are ready to spring into action whenever needed.
Setting up a failover system with one or more redundant installations means that a single power outage or technical server problem won’t cut your clients off from their trusted online channel.
#9. Establish routine reviews of third-party integrations
Assessing any third-party integrations you have in your store and removing ones that have become obsolete or you no longer use ensures you’re minimizing the number of external parties with access to your data.
#10. Adopt a secure payment processing platform
Secure payment processing platforms are like the armored cars of online payment. They protect your financial information for each transaction, ensuring that no credit cards are skimmed or transactions intercepted.
Sana Pay, our in-house payment processor, seamlessly integrates with your web shop and your ERP, allowing your customers to pay securely and directly – all without leaving your e-commerce store.
• Pay orders directly during checkout
• Save payment details for later
• Complete payments quickly
#11. Use a platform you can trust with your data
Make sure to vet your e-commerce provider properly and check that they provide the security measures you need. Sana Commerce takes careful steps to safeguard your web store from potential threats. With multiple layers of security, unauthorized access is difficult. The end result is a process that minimizes the time you’ll need to review security measures, without having to worry things aren’t being done properly. See what security measures Sana Commerce takes to keep you from becoming vulnerable.
Optimizing your web store’s e-commerce security practices ensures you can protect sensitive data, stay scalable, and most importantly, prioritize the relationships you’ve established with your customers. With the right tooling, and by remaining alert to your online portal’s vulnerabilities, maintaining high security standards becomes a simple matter of practice.

The brand new report for IT leaders across industries
Poor B2B e-commerce can have a seriously damaging ripple effect. Learn more in our brand-new report.




